How much do secure, efficient computing and monetary stability matter to you ?
Virtually all 21st century business operators and investors face two core challenges : 1) leveraging a secure and efficient computing infrastructure and 2) maintaining business continuity through underlying monetary instability. This article lays out how JWRD(i) Computing works with clients to convert these challenges into a competitive advantage.
The challenge of deploying and maintaining secure and efficient computing infrastructure comes into play on all levels of the supply chain ; from communications to analytics to contracts to payments to financial instruments and markets to even as deep as money itself, computers and the Internet have become integral tools in commerce and finance. Security and efficiency are powers derived from underlying understanding and control over one's environment.
The modern market has become flooded with computing solutions pushed by big corporations which are proprietary, costly and take away control of crucial infrastructure and even data, leaving businesses more exposed to counterparty risk from their vendors. Businesses that want to retain or regain such control have been left with dwindling options and the stakes continue to rise.
Fronts where control has been ceded and resulting counterparty risk has risen include :
- Access to and compilation of source code(ii) on every level from firmware to operating system to applications.
- In 2015, spyware was planted (archived) in the Apple developer toolchain, which was then propagated to over 4,000 iOS applications available in their App Store.
- Since ~2008, all Intel chips have been infected with their Management Engine at the Basic Input Output System (BIOS) level. The Management Engine system allows Intel to remotely exfiltrate information from the machine even when powered off. Intel prevents the owner of the machine from replacing Intel's code with independently compiled code. This is essentially a backdoor enabling Intel, or anyone who gains access to Intel's system, to access your information at will and likely without your notice.
- Operating Systems such as Microsoft Windows compound the risk factors of proprietary code with being over-engineered and unnecessarily complex. This makes them more prone to error and seemingly necessitates regular changes to the system pushed by Microsoft. The supposed owner of the system is not able to effectively verify the code being installed in the updates pushed and it's often the case that supposed fixes to old bugs introduce new bugs.
- The downsides of third-party compiled code are amplified by increased reliance on cloud based solutions. "The cloud" is really marketing speak for some machine owned by someone else which provides that someone else(iii) full access to what was your sensitive information.
- For example, in 2012, 47k BTC was declared to be lost by two companies using Linode, a Virtual Private Server (VPS)(iv) provider.
- Closer to the cause of the preceding points is the pervading industry fashion we refer to as "fast food computing". Fast food computing is the expectation an outside corporation will provide marginally convenient solutions that are cheap in the short-term and that the user need not know the ingredients nor inner workings.
Ceding control to a third party makes one more dependent and fragile. JWRD Computing exists to save our clients time and money in the process of putting them firmly back in full control of their own digital infrastructure -- i.e. helping them regain personal sovereignty. We work from the principles of comprehensibility toward the goal of intellectual ownership for our clients of all the products and services we provide. Our service allows clients to mitigate the risk of unexpected catastrophic expenses and focus on improving efficiency and capitalizing on opportunities to grow their business.
Maintaining business continuity through monetary instability. The multi-decade, unprecedented experiment of high inflation(v) global central banks have been engaged in has incentivized unsustainable debt levels that have made corporations and governments alike fragile and desperate. Evidence continues to mount that central bankers and politicians are more likely to continue to devalue the purchasing power through adding zeros to the end of accounts on the central server(vi) and attack the fungibility of the currencies they monopolize than to admit they've been wrong. The risks to business operators and investors include :
- the fiduciary being forced by government to freeze funds or deny transactions ;
- insolvency of the fiduciary ;
- arbitrary wealth tax ;
- insolvency of government deposit insurance ;
- negative interest rates ;
- central bank inflation that dilutes purchasing power and is steadily ratcheting the risk of Weimar/Zimbabwe/Venezuela style hyperinflation.
Bitcoin(vii) was designed to thrive in an such an environment. While Bitcoin provides owners several cutting edge advantages, it comes with its own additional set of security challenges. JWRD provides clients with hardware, software and operator training to mitigate risks and fully capture the upside of Bitcoin payments and custody.
What we've done to confront these challenges.
We've developed solutions on three major fronts.
- Hardware :
- Secure Key Management Hardware Package ;
- Build recipes and configurations for Corebootable Hardware ;
- Build and configuration recipes for Router ;
- Standard Operating Procedures for airgap operation via Optical Data Diode ;
- Procurement of Hardware Random Number Generators ;
- Faraday cage design and implementation.
- Custom Software :
- Gales Linux(viii), among other security advantages, it's one of the only Linux distributions which provides the operator the independence to compile all source code ;
- Gales Bitcoin Wallet (GBW) : designed to be used over an airgapped system. The offline signing component is written in Gales Scheme(ix).
- Code contributions(x) to the Bitcoin reference implementation, i.e. The Real Bitcoin (TRB)
- yrc, the Unix Internet Relay Chat (IRC) client. Common modern chat services require the use of the providers' proprietary software clients and servers. IRC is an Internet Standard chat protocol which can be deployed to implement your own privately operated chat network.
- Operator training curriculum covering :
- Unix command line operation ;
- System and Network Administration ;
- Secure Key Management ;
- Encryption/Cryptographic Signing Software, Gnu Privacy Guard (GPG) ;
- V, TRB and GBW installation, configuration and usage.
What we offer.
We provide design consulting, support, custom software development, and hardware packages that match your needs. Below are some examples of what we provide :
Option 1 : Consulting, System Administration and Development :
For businesses with deployed systems we provide auditing, consultation system administration and development services to improve the efficiency and security of extant tools and operations. Auditing and consulting clients receive a report that reviews the strengths of current infrastructure and procedures and provides recommended plans and quotes for strengthening weaknesses.
Our System Administration and Development experience includes :
- Windows, Mac, Linux, Unix and BSD operating systems ;
- VMware and KVM virtualization ;
- ERP and CRM software configurations ;
- a variety of apps & protocols, databases, hardware, networking and monitoring ;
- custom browser configurations and secure password management procedures ;
- software development in 10+ programming languages.
Our personnel has experience deploying everything from ancient POWER servers needing custom-wired serial cables to SPARC to modern HP blade systems and more in between. Given the flexibility of this service, the pricing varies per project ; email us at sales (at) jwrd.net today to get started on tailoring a solution to you.
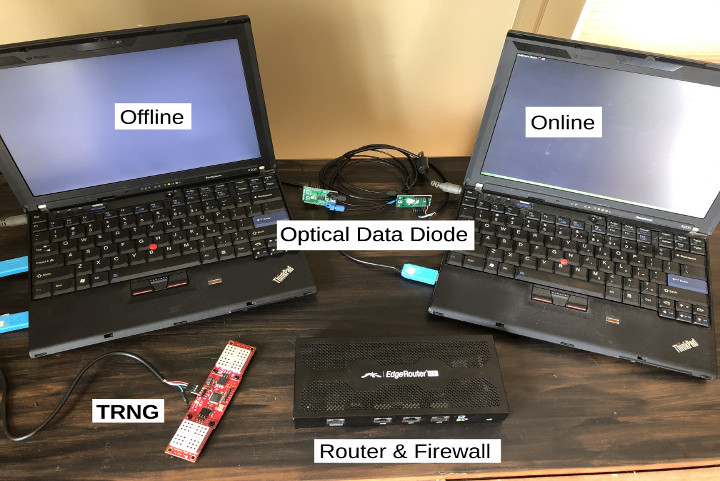
Option 2 : Key Management Hardware Package :
This package includes two Corebootable(xi) laptops (one for offline and one for online use), an optical data diode for securely transferring data between online and offline systems, a Hardware True Random Number Generator (TRNG)(xii) and a router.
|
|
Option 3 : Operator Training :
We distinguish ourselves methodologically by working from the root axiom of V, to quote:
Software is the property of people running it, and part of the systems running it.
We execute on this by providing clients a system reduced to essential complexity and training on operating the system from a well-established and high leverage tool, i.e. the Unix command line. With the skills to operate in a text-only environment, they're afforded the double advantage of 1) improving their security by saving millions of lines of complex and often unsafe code --measuring often in Gigabytes, used to commonly implement the mouse-driven(xiii) graphical user interfaces (GUI) and 2) improving their skills, mindset and efficiency through learning the command line(xiv).
Training sessions and homework assignments to develop following knowledge and skills:
- Beginner : 9 sessions, $3,600. All delivered remotely, no hardware purchase required.
- Unix command line operation ;
- The advantages of plain text as the universal interface ;
- Intermediate file system theory and practice ;
- Handy tools in a pure text environment : vim, less, tmux ;
- Intermediate shell usage ;
- Time, File & Stream Management ;
- System and Network administration.
- Intermediate : 10 sessions, $4,000. Requires purchase of one router and one laptop. Price does not include hardware costs.
- Fundamentals of cryptographic key generation and management ;
- GnuPG usage ;
- V - usage of the cryptographic version control system ;
- yrc, the Unix IRC client usage ;
- Router and firewall installation and configuration ;
- Bitcoin node compilation, installation and configuration ;
- Bitcoin node usage ;
- Gales Bitcoin Wallet installation, configuration and usage.
- Advanced : 8 sessions, $3,200. Full Key Management Hardware Package required. Price does not include hardware costs.
- Compilation, installation and configuration of Gales Linux ;
- Compilation and installation of BIOS ;
- Hardware TRNG firmware verification and usage ;
- Optical Data Diode usage.
How does the training work ?
- Placement Testing: All clients take a placement test to determine which level they'll start in.
- Training Options : Study Heavy and Class Heavy.
- Study Heavy : 3 hours independent reading and practice exercises for each hour of training session.
- Class Heavy : 1 hour of independent reading and practice exercises for each hour of training session.
- All sessions are 90 minutes either once or twice a week.
- Exercises and reading are assigned between sessions.
Model Training Pace of Study and Payment Options
The table below breaks down the pricing and time commitment for common examples of study pace and payment options. Receive 5% off when two modules are purchased at a time and 10% off when all modules are purchased upfront. Group sessions of 2 simultaneous clients receive a 10% discount per client and groups of 3 receive a 20% discount, with 3 being the maximum group size.
| Study Heavy | Study Heavy | Class Heavy | Class Heavy | |
|---|---|---|---|---|
| Number of Sessions: | 27 sessions | 27 sessions | 54 Sessions | 54 sessions |
| Study/Session Ratio: | 3:1 | 3:1 | 1:1 | 1:1 |
| Session Time: | 27 x 90 min = 40.5 hrs | 40.5 hrs | 54 x 90 min = 81 hrs | 81 hrs |
| Study Time: | 121.5 hrs | 121.5 hrs | 81 hrs | 81 hrs |
| Time Commitment: | 162 hrs | 162 hrs | 162 hrs | 162 hrs |
| Payment Options : | 3 payments totaling $10,800 | 1 payment of $9,720 | 3 payments totaling $21,000 | 1 payment of $18,900 |
| Cost: | $10,800 | $9,720 | $21,000 | $18,900 |
The Bottom Line result is....
... as our client you break out of the common learned helplessness that herds the mainstream to fit into whatever the mass production line is pumping out and on its schedule too(xv) ; own your complete infrastructure and make it work for you ; lower the cost to understand the software you use by enumerating goodness, minimizing complexity, verifying sources and compiling everything ; becoming a stronger operator through education and practice of sensible skills such that you build the capacity to establish private communications and ownership of money and transactions.
What clients say.
Johan Castellanos, CEO of SayShannon :
"I had no concept what so ever of Linux/Unix but after the course I feel that I can venture into the world of operating systems with confidence and with the assurance that I will find answers."
How does JWRD compare ?
- The Unix command line is the most established and one of the oldest modes of computer operation because of the efficiency and security advantages it provides. It's available natively on Linux, BSD and Mac OS X systems (Mac OS X is derived from BSD). As such, there is an abundance of educational and practical resources available on the web to learn the Unix command line and a reason clients can test out of the Beginner level. Our Unix training balances underlying theory and one-on-one guidance of an expert in practicing the commands to accelerate the learning process. Training is done on Gales Linux and thus clients get direct experience utilizing the design advantages it offers.
- No one we're aware of offers a key management hardware package as thorough we do, which includes Hardware Random Number Generator, Optic Data Diode for Air Gap data transfer, Corebootable machines for both Offline and Online systems and Router installation and configuration.
- No one we're aware of offers training on airgapped Bitcoin wallet or GPG usage.
- The skills and system to safely transact and save in Bitcoin provides a clients power not really comparable to anything else. Where else can you own an arbitrary amount of wealth in a small series of numbers(xvi) ? And furthermore, the power to verify both the money supply and conduct arbitrarily large transactions globally for the cost of a few modestly provisioned computers, internet connection, software that's publicly available and a few weeks worth of dedicated training on the skills to operate the tools ? Even a banking license and underlying capital and competence to make the license economical don't provide you that power.
The Cost of Waiting
- Cryptographically safe hardware is in increasingly limited supply. It is unknown how much remains, we can get you set up quickly while supplies last.
- The cost of our service priced in fiat currencies will rise indefinitely.
- Your personal opportunity cost can only be yours to evaluate, we invite you to consider the value of the results you'll earn for yourself by enhancing your security over your information, computers and money.
How to get started today.
To start the process of regaining your personal sovereignty through strengthening your digital security with JWRD, email us at sales (at) jwrd.net today with your name and a brief description of your interest. If you're interested in a call, include your phone number and a convenient time to reach you.
- Jacob Welsh (WoT : jfw) & Robinson Dorion (WoT : dorion [^]
- People read and write source code. A program called the compiler converts the human readable source code into the machine executable binary code, the latter being exceptionally costly for humans to understand. That is to say, if you're installing third-party compiled binary files (binaries), there is little to no chance you understand what you're actually installing and are thus more at risk to third party malice and incompetence. [^]
- and note, any other third party it's associated with or becomes a target of. [^]
- VPS is a technical lingo for the cloud. [^]
- Meaning the proper definition of inflation, i.e. money supply growth, not that "consumer"/"producer" price propaganda the socialist state has been pushing. For example, the yearly change in Federal Reserve reported M1 since 1971 has a geometric average north of 6%. [^]
- What percentage of USD/EUR/GBP/JPY/CNY is digital after all ? [^]
- The undebaseably scarce, peer-to-peer digital cash, the most robust extant protector of property rights and largest computing network on earth for some years now. Bitcoin supply is undebaseably scarce by definition at the protocol level and through its mathematical properties. Pretty much any natural commodity that has or could in theory serve as money is debaseable either through relatively cheap dilution of impurities, e.g. in 1964 when US silver coins were replaced with nickel plated copper coins, or arbitrary expansion of the supply, e.g. if salt is the money and the king wants more salt he could tax the pepper farmers and invest the proceeds expanding the salt works and supply. Those closest to the new supply (salt, fiat or otherwise) spend it into the economy, bidding up goods and diluting the purchasing power of savers and creditors. [^]
- Reviewed to date by bvt (WoT : bvt), Lucian Mogosanu (WoT : spyked) and Diana Coman (WoT : diana_coman) and on which Mircea Popescu (WoT : mircea_popescu) noted :
mircea_popescu: "A feature that I liked a lot is that shell is the only scripting language in the default install of the distribution. Typically perl and python get pulled in unconditionally as a build dependency of a runtime dependency of some rarely-used default-installed utility, or are directly used to implement package manager, etc. With Gales, a decision about what scripting language to use can be made without constraints created
mircea_popescu: by ready availability of python or others." << indeed this is mindblowingly beautiful, and as far as i current;y know the foremost fearher in jfw 's cap.
mircea_popescu: feather* [^] - Gales Scheme is a dynamic, type-safe, functional programming language. The code is published here on Fixpoint with articles to describe the code pending. Scheme is a well-established, powerful language that is specified in a shade over 50 pages of text. The advantage Gales Scheme provides JWRD clients is superior comprehensibility of mission critical components such as handling the money. [^]
- The code is described and made available on Fixpoint : here and here [^]
- Coreboot is an open source BIOS project that can be used on some machines which do not enforce the Intel Management Engine discussed above. [^]
- To quote from the vendor's website :
Why is entropy important ?
As the old adage goes, "Any one who considers arithmetical methods of producing random digits is living, of course, in a state of sin."Any Turing machine (such as any desktop or laptop computer, tablet, smartphone or other digital device of any type, kind, make or vintage, including without limitation any machinery used by any government for any purpose, be it nuclear tests, space flight, military applications not to mention Tamagotchis and old Nintendo boxes) is, by definition (and without exception possible in theory or ever encountered in practice), a square keyhole. It can be opened equally well by all those who possess the mighty secret of the shape of its key : a square.
Entropy provides the only solution available, and the only solution possible to this problem. The only way known, and the only way that can ever be or will ever be devised to transform a computer into my computer, as a matter of fact rather than an exercise in delusion -- relies on the use of entropy. There is not, nor could there ever be, any alternative.
Consequently, the only fair statement of the situation is to point out that entropy is not merely fundamental, but specifically required for personal as opposed to collectivist computing ; and as technological development pushes society further into the digital age, entropy becomes ever more central as the only available building block of individual existence. In short : without entropy, you don't exist, because without entropy -- there is no you, there's only a morass of "us".
[^]
- A.k.a. point and click, click and cluck, etc. [^]
- To help those readers who've never considered the advantages of the command line interface (cli) begin to conceptualize what they've been missing, I invite you to reflect on the fact a supreme authority compared it to discovering sight after living in a state of blindness, to quote:
disability. in terms of severity, blindness compares, deafness does not. obviously the afflicted are scarcely aware, but this doesn't mean they're not afflicted.mircea_popescu: the fundamental problems are that cli-iliteracy is a serious, life-changing
mircea_popescu: whole "work-years", entire "departments" could readily be replaced by you know, half hour's worth of sed ; they aren't because us corporatelandia mostly exists as makework, to create the illusion for millions of ambitious derps that they're "doing something" lest they take to the streets and start throwing rocks. nevertheless, even if the cutting legs is systematically needed in socialism, to crate the sort of helpless vat
mircea_popescu: -people it can thrive amongst, it's still personally disabling.
mircea_popescu: so you know, as far as the life prospects, the future evolution, however you will name the sum-total potential of a person's existence, understanding how to command line is more important than meeting their father. it'll certaily do a lot for them, and it certainly CAN do way the fuck more for them.
mircea_popescu: gales or no gales, the man who can't cat | grep is closer to a boy than any other man.
mircea_popescu: http://logs.ossasepia.com/log/trilema/2020-01-24#1957189 << quite so. using tools, ~thinking in ways which make their activity amenable to useful tools~ and so on.
ossabot: Logged on 2020-01-24 19:54:12 jfw: http://logs.ossasepia.com/log/trilema/2020-01-24#1957173 - regarding the "because" there: there was perhaps a degree of teaching it because we'd built it, but I see it more the other way - a text-only Linux being a good choice for the job specifically because it doesn't have the GUI crutch and CLI illiteracy is one of the bigger barriers that otherwise intelligent people face to using serious[^]
- Apple's planned obsolescence scam may come to mind about now. [^]
- i.e. the private key which in Bitcoin is 256 bits. The advantage of it being physically small is it lowers your cost to hide, protect and transport. [^]
[...] congrats dorion on publishing that sales article [...]
Pingback by #ossasepia Logs for May 2020 « Ossa Sepia — May 3, 2020 @ 19:06
[...] JWRD – learn how to use a computer, sort out secure Bitcoin [...]
Pingback by Credenda, Agenda « Young Hands Club — September 12, 2020 @ 21:20
[...] This looks like exactly what I’m after. I should’ve engaged with these guys while YH was open, and started building relationships with people. Still – no time like the present! There’s value beyond the training/software/hardware: interacting with cool people. [...]
Pingback by Initial Thoughts and Questions on JWRD « Young Hands Club — September 30, 2020 @ 12:42
[...] few sessions into JWRD, it occurs to me that I've never really understood what I'm doing when it comes to computers. I [...]
Pingback by Does Not Compute « Young Hands Club — November 1, 2020 @ 04:15
Updated to include Diana's article on Gales Linux, which I somehow failed to include in the original.
Comment by Robinson Dorion — April 30, 2021 @ 03:33
[...] It's high time I captured the previously oral, informal or otherwise behind-closed-doors introduction to the hardware package we've been selling slowly but steadily for some years now. [...]
Pingback by Getting started with the JWRD key management hardware kit « Fixpoint — February 28, 2023 @ 07:37
[...] an informed operator. So ask yourself, are you working today to strengthen your grip on things that matter [...]
Pingback by The ownership of Bitcoin : custody, transactions and dispute resolution. « Dorion Mode — April 4, 2023 @ 21:21
[...] and Greenfin and their fee simple, syntax destroying nonsense ? Or are you going to learn to start protecting what matters strengthen your grip such that you can hold the digital alodial title that is Bitcoin and [...]
Pingback by Syntax destruction is the fountainhead of fiat propaganda on Dorion Mode — April 14, 2023 @ 03:37
[...] be all, cheers ! For the things that matter, Linux is pretty much your only option, bitch. [^]One of the reasons he's a reader is so he doesn't [...]
Pingback by The Junto, by JWRD on Dorion Mode - A blog by Robinson Dorion. — May 25, 2023 @ 19:02
In your opinion if you only had one Coreboot laptop is it more important to use it on the offline computer or use it on the online node? I will try to obtain another but for now it's a normal x200.
Thanks.
Comment by bits — October 25, 2025 @ 20:23
@bits
It's an interesting question.
On the one hand, from a personal perspective, the offline machine may seem more important since it's handling your sensitive signing information and the blockchain information can be obtained and cross referenced from a number of different sources.
On the other hand, if the offline is truly airgapped, it seems rather unrealistic to attack by a bios based exploit, whereas an online machine might benefit more.
From a network perspective, it's vital that at least some nodes are running Coreboot.
We only sell the normal x200, not the x200s.
I hope this reply is helpful, even if it doesn't give you a definitive answer. In any case, make sure you have a strong source of entropy/randomness for your key generation and transaction signing operations.
Comment by Robinson Dorion — November 3, 2025 @ 22:01